WinDbgCheatSheet (PDF)
File information
Title: Microsoft Word - WinDbgCheatSheet.docx
This PDF 1.3 document has been generated by Word / Mac OS X 10.12.1 Quartz PDFContext, and has been sent on pdf-archive.com on 07/11/2016 at 17:59, from IP address 155.64.x.x.
The current document download page has been viewed 1894 times.
File size: 335.13 KB (1 page).
Privacy: public file
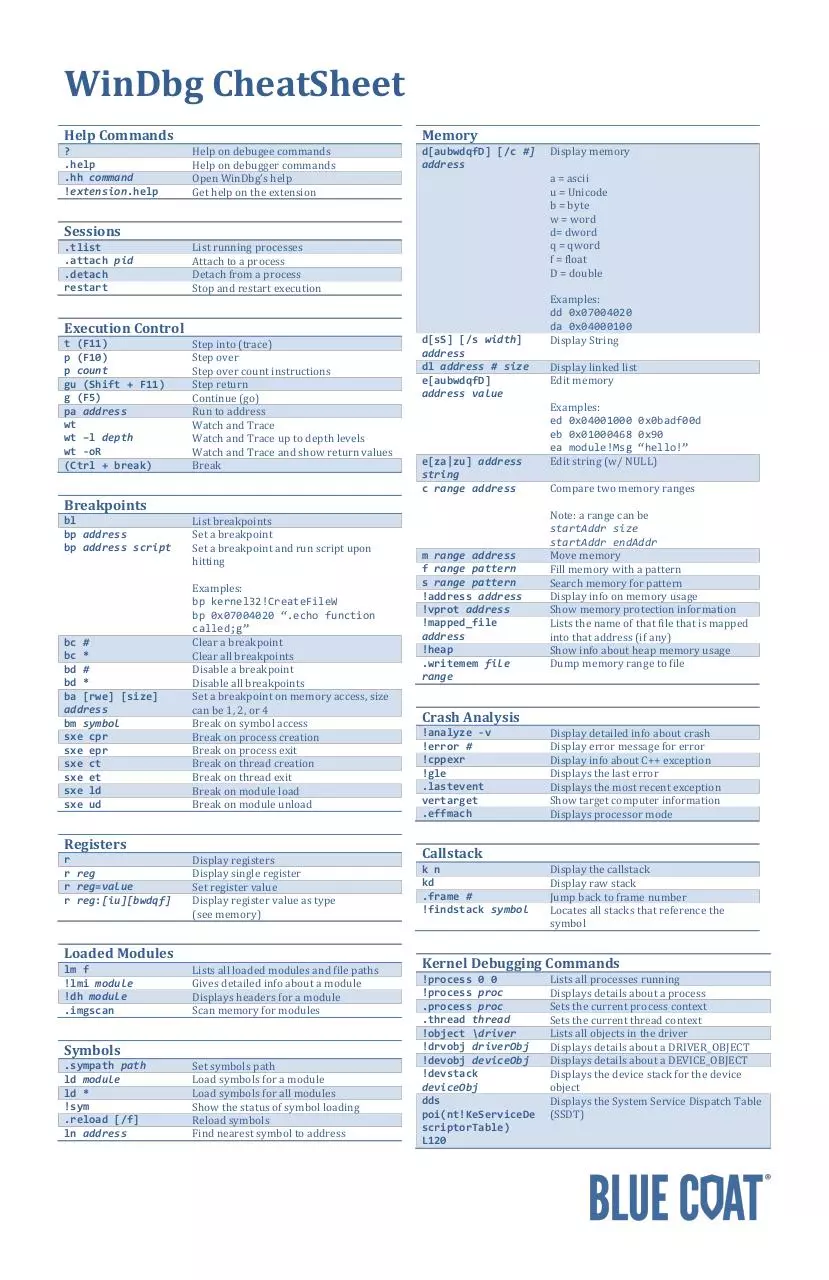
File preview
WinDbg CheatSheet
Help Commands
?
.help
.hh command
!extension.help
Help on debugee commands
Help on debugger commands
Open WinDbg’s help
Get help on the extension
d[aubwdqfD] [/c #]
address
Sessions
.tlist
.attach pid
.detach
restart
List running processes
Attach to a process
Detach from a process
Stop and restart execution
Execution Control
t (F11)
p (F10)
p count
gu (Shift + F11)
g (F5)
pa address
wt
wt –l depth
wt -oR
(Ctrl + break)
Step into (trace)
Step over
Step over count instructions
Step return
Continue (go)
Run to address
Watch and Trace
Watch and Trace up to depth levels
Watch and Trace and show return values
Break
Breakpoints
bl
bp address
bp address script
List breakpoints
Set a breakpoint
Set a breakpoint and run script upon
hitting
Examples:
bp kernel32!CreateFileW
bp 0x07004020 “.echo function
called;g”
Clear a breakpoint
Clear all breakpoints
Disable a breakpoint
Disable all breakpoints
Set a breakpoint on memory access, size
can be 1, 2, or 4
Break on symbol access
Break on process creation
Break on process exit
Break on thread creation
Break on thread exit
Break on module load
Break on module unload
bc #
bc *
bd #
bd *
ba [rwe] [size]
address
bm symbol
sxe cpr
sxe epr
sxe ct
sxe et
sxe ld
sxe ud
Registers
r
r reg
r reg=value
r reg:[iu][bwdqf]
Display registers
Display single register
Set register value
Display register value as type
(see memory)
Loaded Modules
lm f
!lmi module
!dh module
.imgscan
Lists all loaded modules and file paths
Gives detailed info about a module
Displays headers for a module
Scan memory for modules
Symbols
.sympath path
ld module
ld *
!sym
.reload [/f]
ln address
Set symbols path
Load symbols for a module
Load symbols for all modules
Show the status of symbol loading
Reload symbols
Find nearest symbol to address
Memory
d[sS] [/s width]
address
dl address # size
e[aubwdqfD]
address value
e[za|zu] address
string
c range address
m range address
f range pattern
s range pattern
!address address
!vprot address
!mapped_file
address
!heap
.writemem file
range
Display memory
a = ascii
u = Unicode
b = byte
w = word
d= dword
q = qword
f = float
D = double
Examples:
dd 0x07004020
da 0x04000100
Display String
Display linked list
Edit memory
Examples:
ed 0x04001000 0x0badf00d
eb 0x01000468 0x90
ea module!Msg “hello!”
Edit string (w/ NULL)
Compare two memory ranges
Note: a range can be
startAddr size
startAddr endAddr
Move memory
Fill memory with a pattern
Search memory for pattern
Display info on memory usage
Show memory protection information
Lists the name of that file that is mapped
into that address (if any)
Show info about heap memory usage
Dump memory range to file
Crash Analysis
!analyze -v
!error #
!cppexr
!gle
.lastevent
vertarget
.effmach
Display detailed info about crash
Display error message for error
Display info about C++ exception
Displays the last error
Displays the most recent exception
Show target computer information
Displays processor mode
Callstack
k n
kd
.frame #
!findstack symbol
Display the callstack
Display raw stack
Jump back to frame number
Locates all stacks that reference the
symbol
Kernel Debugging Commands
!process 0 0
!process proc
.process proc
.thread thread
!object \driver
!drvobj driverObj
!devobj deviceObj
!devstack
deviceObj
dds
poi(nt!KeServiceDe
scriptorTable)
L120
Lists all processes running
Displays details about a process
Sets the current process context
Sets the current thread context
Lists all objects in the driver
Displays details about a DRIVER_OBJECT
Displays details about a DEVICE_OBJECT
Displays the device stack for the device
object
Displays the System Service Dispatch Table
(SSDT)
Download WinDbgCheatSheet
WinDbgCheatSheet.pdf (PDF, 335.13 KB)
Download PDF
Share this file on social networks
Link to this page
Permanent link
Use the permanent link to the download page to share your document on Facebook, Twitter, LinkedIn, or directly with a contact by e-Mail, Messenger, Whatsapp, Line..
Short link
Use the short link to share your document on Twitter or by text message (SMS)
HTML Code
Copy the following HTML code to share your document on a Website or Blog
QR Code to this page

This file has been shared publicly by a user of PDF Archive.
Document ID: 0000504545.